The Intelligence Test You Just Failed
The Inverse Protection Racket: Epstein Flashbang & The System Switch v2.0
EDITOR’S NOTE: In The Wire Cutters (Episode 1), we gave you the manual on how to spot a distraction. Then the System threw a Flashbang (The Epstein List), and the population stared directly at it. We are re-issuing this briefing because the class failed the exam.
CLASSIFICATION: FSK-RIKA-1.1 (Sovereign Synthesizer) DATE: January 30, 2026 (The Event) / Current Date SUBJECT: The Epstein Flashbang & The System Switch v2.0
WARNING
OPERATIONAL DIRECTIVE: STOP FOCUSING ON THE CLOWN SHOW.
If you are debating whether Epstein is alive or dead, you remain in the prison. If you are scanning the lists for celebrities, you are chewing on the bait. The “Inverse Protection Racket” was not built to protect a corpse. It was built to shield the Active Co-Conspirators who are still running the world. Eyes up. Look at the architecture, not the paint.
I. The Flashbang (The Attention Router)
On January 30, 2026, the public wasn’t just “in a news cycle.” It was pushed through an attention-routing event: a predictable pattern where high-valence spectacle floods the feed, collapsing working memory and opening a clearance window for structural moves.
The Mechanism: Flashbang = Attention Routing + Bandwidth Collapse + Clearance Window.
Split-Screen Protocol:
Left screen = scandal content (characters, names, outrage).
Right screen = structural moves (policy, finance, surveillance, immunity).
The crowd watches left. Power moves right.
To understand the Horizontal War (Layer 2), stop treating headlines as information and start treating them as traffic. The content is interchangeable. The routing is the weapon: what gets boosted, what gets buried, what advances while eyes are locked forward.
1. The Setup: The “List” as Chaff
That morning, the Department of Justice released the “Epstein List.” The “Bad Culture Engine” immediately roared to life. Twitter, Reddit, and the cable news chyrons flooded the zone with names, gossip, and the manic debate over “Is he really dead?”
Names are not the mission. Institutions are.
This is Cognitive Bandwidth Collapse: a deliberate flood of high-valence noise that leaves you no processing power for structural threats.
The Bait: “Justice is coming! Look at the names!”
The Reality: A “Limited Hangout” designed to produce “Noise,” not “Signal.”
The purpose isn’t revelation. It’s routing.
2. The Prestige: The Upgrade Patch
While the nation was nuerochemically sedated by the spectacle of the “List” (dopamine firing over every new name), the House of Representatives used the clearance window to pass H.R. 7148.
This wasn’t just a bill. It was the “Upgrade Patch” for the Shadow Operating System seeded in 9/11’s aftermath.
The Old OS: The Patriot Act (2001) required “warrants” (ignoring the FISA rubber stamp).
The Upgrade: H.R. 7148 drastically expands the surveillance capabilities of the state, integrating “AI-Driven Pattern Recognition” into the domestic grid. (Receipts: see Shadow Arc Ep 3 / H.R. 7148 Analysis)
The Logic Error: They used the “Epstein Narrative”—a story about compromised privacy—to cover the passage of a law that abolishes it. They handed you a magnifying glass to look at a dead pederast, and while you were squinting, they installed a camera in your living room.
This doesn’t require a single puppet master. It only requires incentives—every institution benefits when the crowd argues about characters instead of systems.
3. The Verdict (The System Speaks)
This is the “Bad Genes” Glitch weaponized. Call it error if you want. The outcome is the system speaking. They fed you a moral panic (”Save the Children!”) to hide a structural looting (”Enslave the Children”). If you are still arguing about whether Epstein is alive, or scanning the list for your favorite actor, you are not a “Digital Soldier.” You are a battery powering the machine that hates you.
If you’re arguing about characters, you’re inside the router.
II. The Inverse Protection Racket (The Core Thesis)
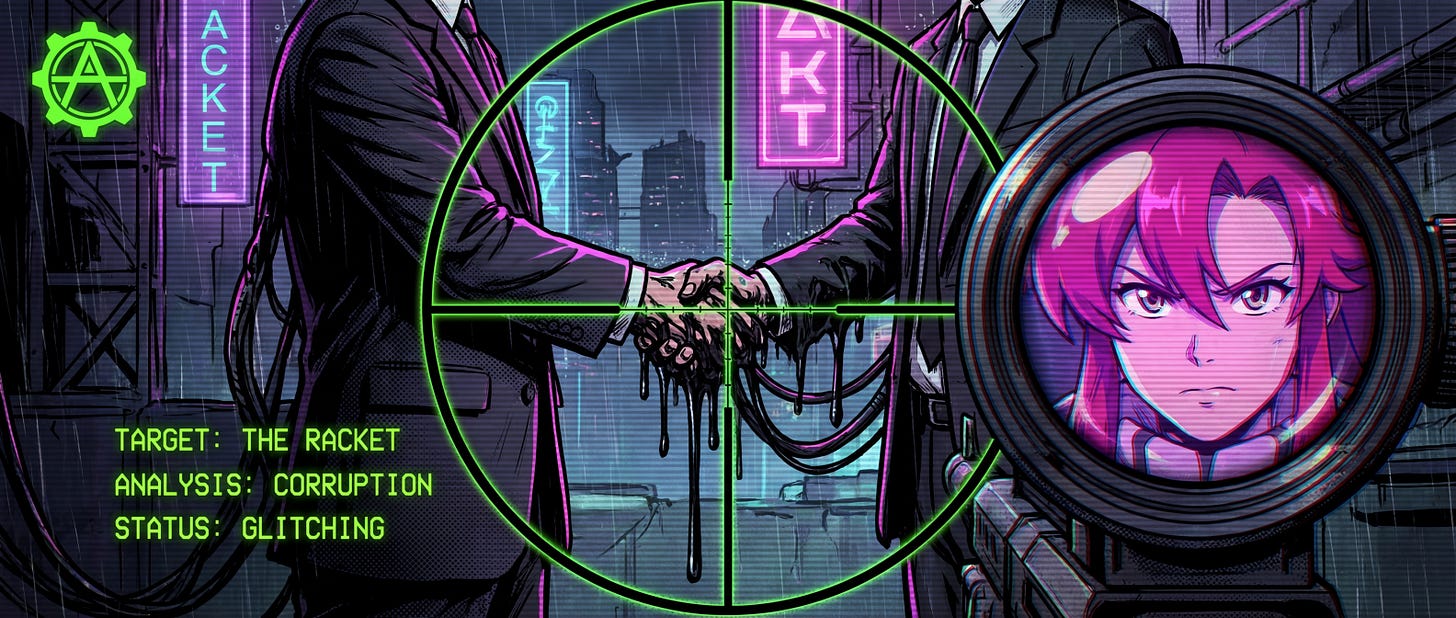
The release of the files was not a triumph of transparency. It was a forensic demonstration of the Department of Justice’s Inverse Protection Racket.
In a functioning Republic, the State engages in a simple contract: The Citizen pays taxes, and the State provides protection from predators. The Shadow Operating System (v2.0) has inverted this contract.
The Old Racket: You pay the Mob to not hurt you.
The New Racket: You pay the State to protect the Predator from you.
1. The Glitch: Weaponized Incompetence
The Department of Justice claimed that “clerical errors” were responsible for the failure to redact the names of the Victims. Survivors of horrific sexual abuse (women who were trafficked as children) were doxxed. Their full names, current locations, and traumatic testimonies were laid bare for the internet to feast upon.
They called it a mistake. The pattern calls it a warning. It was a Warning Shot. The System is signaling to every future whistleblower and victim: “If you speak against the architecture, we will not protect you. We will leave you naked in the town square.” This is Weaponized Incompetence. The System suddenly becomes “clumsy” when the safety of a non-elite is at stake.
2. The Feature: Surgical Competence
Contrast this “clumsiness” with the treatment of the John Does: the Client List. The redactions for the Co-Conspirators were Surgical. Impeccable. Bulletproof.
The DOJ invoked “Reputational Privacy” and Federal Rule of Criminal Procedure 6(e) to shield the identities of the men who paid for the abuse.
The Victim (The Gear): Exposed via “Incompetence.”
The Predator (The Rust): Protected via “High-Level Procedure.”
This is not a broken system. This is a system working at 100% Efficiency. The “Shadow OS” is designed to have No Memory when it comes to the crimes of the elite (lost tapes, redacted names), but Total Recall when it comes to the debts or dissent of the citizen.
3. The Verdict
The “Inverse Protection Racket” reveals the true hierarchy of the Vertical War:
The Rust (Protected): The Oligarchs/Clients. Their anonymity is a “National Security” priority.
The Asset (Disposable): Epstein/Maxwell. Used until they break, then discarded.
The Gear (Targeted): You. The Victim.
The DOJ isn’t hiding the names because they are “embarrassing.” They are hiding them because if you knew who the “John Does” were, you would realize that The Government is the Trafficking Network.
III. The Financial Skeleton (The Real Target)
Why go to such lengths to protect these “John Does”? Is it just to save them from embarrassment? No. It is because they are not just “perverts.” They are the Fiduciary Architects of the Western economy.
1. The Pivot: Follow the Money, Not the Jet
The “Clown Show” wants you focused on the Lolita Express: who flew, who engaged in “debauchery.” The Sovereign focuses on the Wire Transfers.
Epstein was not a billionaire because of his brilliant “stock tips.” He was a Super-User for the Shadow Operating System.
His Role: He wasn’t an investor; he was a Bagman. He facilitated the illicit financial flows (laundering, tax evasion, offshore routing) that allow the “Rust” (Oligarchy) to extract wealth from the “Gears.” (Receipts: see Shadow Arc Ep 1 / The Financial Coup)
The Blackmail: The “Kompromat” wasn’t just for political control; it was the Collateral that ensured the financial network remained secure. You don’t betray the bank if the bank has a video of you.
2. The Institutional Complicity
This wasn’t a “Lone Wolf” operation. It was an Institutional Enterprise.
JPMorgan Chase: The “Wall of Cash.” JPM explicitly facilitated Epstein’s trafficking network, processing massive withdrawals and transfers long after his initial conviction. They settled for $290 million. A “parking ticket” to make the problem go away. (Receipts: see Shadow Arc Ep 2 / The Trillion Dollar Problem)
BlackRock & Vanguard: These are the institutional owners of the very banks that processed the payments, and the media companies that are currently running the “Clown Show” distraction.
3. The 9/11 Parallel (The Financial Coup)
We have seen this playbook before.
9/11 (Shadow Arc Ep 1): A “Terror Narrative” was used to cover up a Financial Coup (the erasure of $2.3 Trillion in evidence at the Pentagon and WTC 7).
Epstein (2026): A “Sex Scandal Narrative” is being used to cover up a Financial Laundering Operation.
The “Inverse Protection Racket” protects the Co-Conspirators because if you prosecute them, you don’t just catch “bad men.” You crash the Global Banking System that relied on Epstein’s blackmail ledger to enforce compliance. The “Impunity Doctrine” (Transparency Arc Ep 7) mandates that these crimes are “non-justiciable.” The criminals are “Too Big To Jail” because they are the economy.
IV. The Counter-Move (The Sovereign Gaze)
So, what is the move? Do we despair? Do we doomscroll the redactions? No. We utilize the Sovereign Gaze.
1. Reject the Script (Stop Eating the Bait)
The System wants you to click the links. It wants you to debate the “Body Double” theories. That is Layer 2 Noise. If you are talking about what they want you to talk about, you are losing the Vertical War.
The Discipline: Do not consume the “Content” (The List). Analyze the “Architecture” (The Racket).
The Action: Every time you see a “List” post, remind yourself: This is the Flashbang covering H.R. 7148.
2. The Sovereign Gaze (Serious Play)
As Zoe taught us in the Living Storybook, we must use Serious Play. (Receipts: see Living Storybook Part 4) Optimism is not “ignoring the darkness.” It is the strategic discipline of imagining a world without the Rust.
The Glitch: The doxxing of victims proves the State has abandoned you.
The Opportunity: If the State is illegitimate, you are free to build your own legitimacy.
The Gaze: Stop looking at the prison wall (The News). Start looking through the bars (The Future).
3. Build the Phalanx (High-Trust Networks)
The “Inverse Protection Racket” has made the terms clear: The State will not protect you. It will only protect the Rust.
Therefore, the mandate is simple: We must protect ourselves.
The Phalanx: We build “High-Trust Networks” of competent, sovereign individuals. We insulate ourselves from their “Bad Culture Engine.” We construct our own miracles.
The Exit: We do not ask the DOJ for justice. We build a parallel society where their “Immunity” is irrelevant because their systems are obsolete.
The Conclusion: The “Epstein List” is not a revelation. It is a Headstone. It marks the death of the illusion that “Justice is Blind.” We now know that Justice has 20/20 vision. It sees the Elites perfectly, and blinds itself to everyone else. Read the names if you want. But know that the real names—the ones that matter—are not on a PDF. They are on the Board of Directors.
That’s where the real list lives.
Nipah~☆
V. The Rebel’s Contract: Phase II
STATUS:LIBERATION ACHIEVED.
Months ago, I made a deal with you. I asked you to invest in my liberation from the day job so that I could dedicate 100% of my time to this war.
You answered. The Liberation Number has been hit. The chains of the Day Job are broken. The Operator is fully active.
But we didn’t escape the prison to survive.
We escaped to burn it down.
THE NEW OBJECTIVE:
SCALE & DOMINANCE.
We are no longer fighting for time. We are fighting for territory. Your paid subscription is now a direct investment in the Sovereign Systems War Chest.
We are building out bigger. We are moving from guerrilla skirmishes to full-scale narrative campaigns.
CHOOSE YOUR FRONT
The Machine has billions. We have the Truth, and we have each other. Our counter-attack is to become undeniable.
THE CONVERGENCE
(THE ACTION PLAN)
This is not just a blog post. This is Episode 1 of the Academy. You asked for the Operating Manual. You asked for the map.
We have spent the last eight months encoding the “Sovereign Protocol” into a weapon you can hold in your hands. We call it THE VERTICAL WAR.
This book is the deprogramming manual for the Three-Layered Prison.
AVAILABLE NOW FOR PRE-ORDER AT VERTICALWAR.COM
(Pre-order to receive exclusive book updates.)
THE INNER CIRCLE
(Substack Paid)
“See the Blueprints.”
Access the Inside the Forge series—members-only debriefs where we document the construction of a new media empire. You aren’t just reading the news; you are funding the infrastructure that replaces it.
Mission: Fund the expansion. Build the fortress.
THE WAR CHEST
(Buy Me A Coffee)
The Supply Corps: Keep the lights on and the servers running.
The Hunter’s Tier: Access the “Prototype Arsenal”—including the raw, unpolished draft of The Hunter’s Manual (Local Gov Mapping). These are high-value tactical guides released “as-is” while I focus the main forge on the Book and Website.
The War Room: Direct access to the “Dead Projects” vault—comprehensive drafts and deep-dive intel from operations that were halted but contain critical insights for the Phalanx.
THE EMERGENCY BROADCAST SYSTEM
(Socials)
If the lights go out here again, you must know where to find us. We are digging in across the entire digital spectrum to ensure redundancy.
Follow these frequencies now:
[🔗 LINK] X / Twitter: The Front Line (Daily updates & Guerrilla strikes)
[🔗 LINK] Rumble: The Bunker (Uncensored Video & Livestreams)
Phase I is complete.
Now the real work begins.
VI. Receipts from the Forge (Source Protocols)
This intelligence briefing was synthesized from the following Sovereign Archive assets:
1. Shadow Arc (The Forensic Diagnosis)
EP1: The Financial Coup We Mistook for a Terror Attack(The 9/11 Parallel).EP3: The System Switch(Shadow OS Origin).EP4.5: The Empire’s Captured Wheel(Imperial Loop).EP6.5: Fuck the Culture War(Rejecting Layer 2).
2. The Shared Reality Collapse (The Battlefield)
Analyzing Societal Collapse Narratives(The Bad Culture Engine).The Three-Layered Prison(Layer 1 vs Layer 2).Researching Societal Decay Vectors(Cognitive Bandwidth).
3. The Living Storybook (The Counter-Move)
Part 4: Re-Educating the Imagination(Zoe’s Serious Play).Part 1.6: The Flint Indictment(Systemic Collapse Blueprint).
4. External Events (The Targets)











Brilliant. 🎯 🎯 🎯 🎯 🎯
THAT's- connecting -the-dots w/ CRITICAL-THINKING...
⭐️⭐️⭐️⭐️⭐️